MISP 2.4.183 released with new ECS log feature, improvements and bugs fixed
MISP 2.4.183 released with a new ECS log feature, improvements and bugs fixed.
- MISP now supports Elastic Common Schema (ECS) security logging. A new option has been added
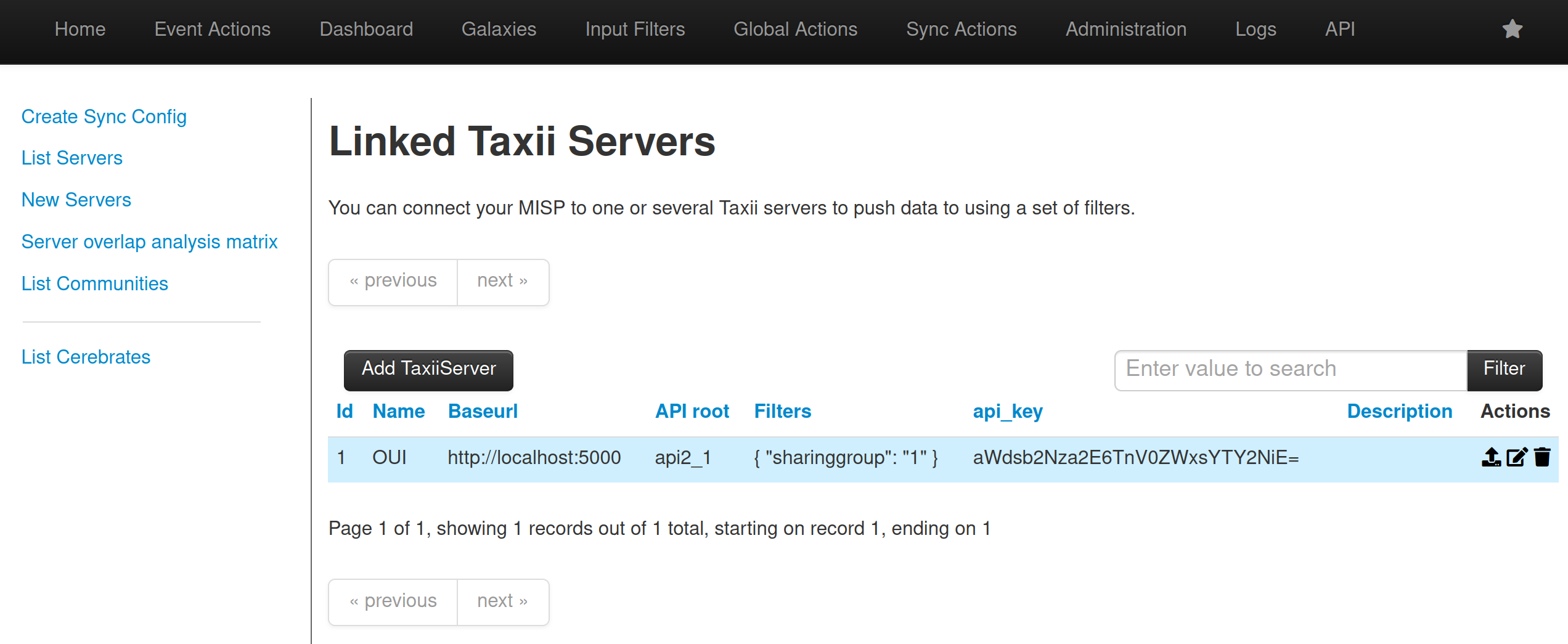
Security.ecs_logto enable this new functionality. A newSecurity.alert_on_suspicious_loginsto security audit has been added. - The sync configuration in MISP now supports sharing group blueprints for a simple creation of filter rules based on dynamically updated organisation lists.
- Major improvement to STIX import handling and especially the misp-stix library such as Parsing PE binary extensions within File observable objects and many more improvements/fixes.
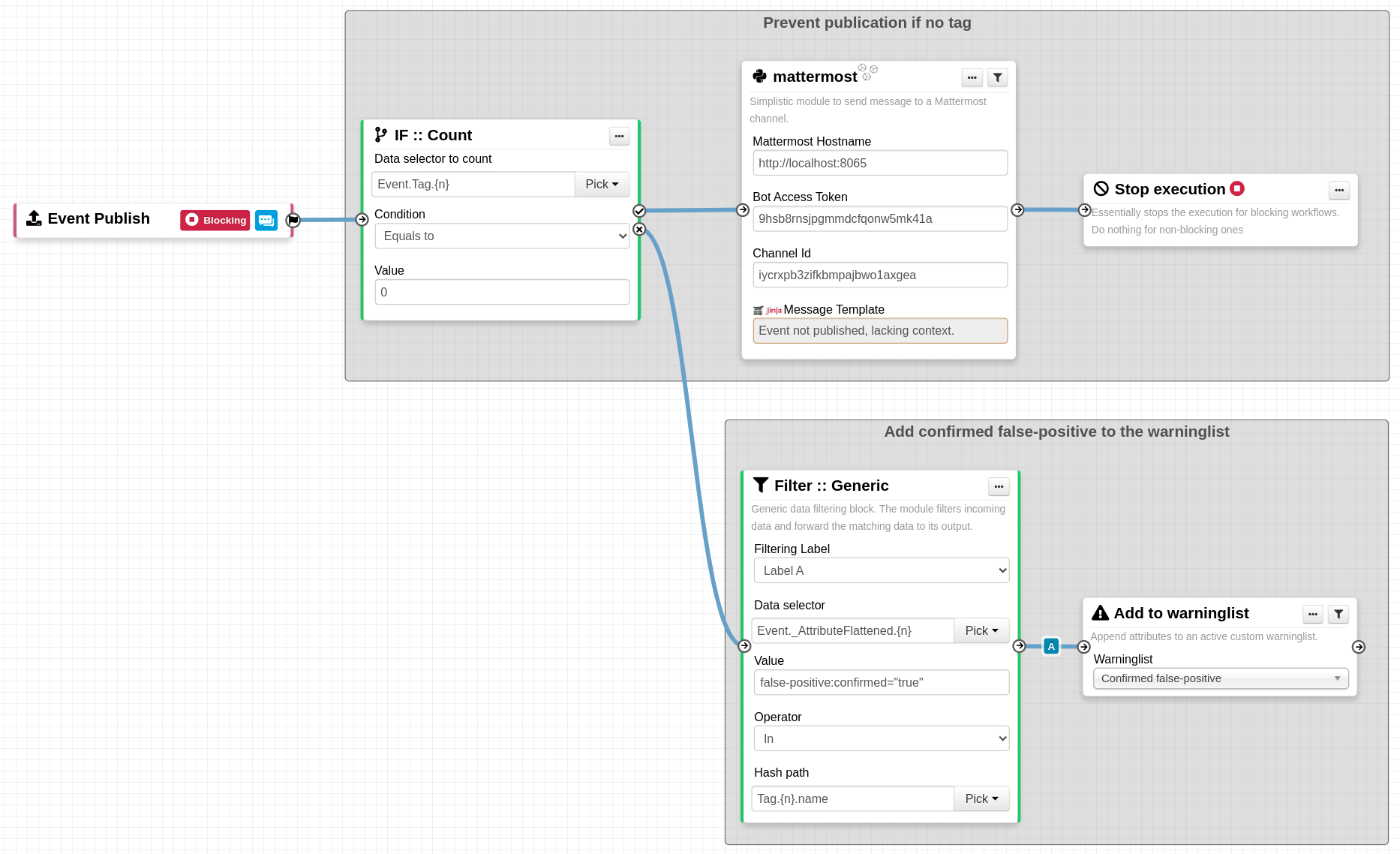
- API add tag functions updated to also work with uuids, rather than just local IDs.
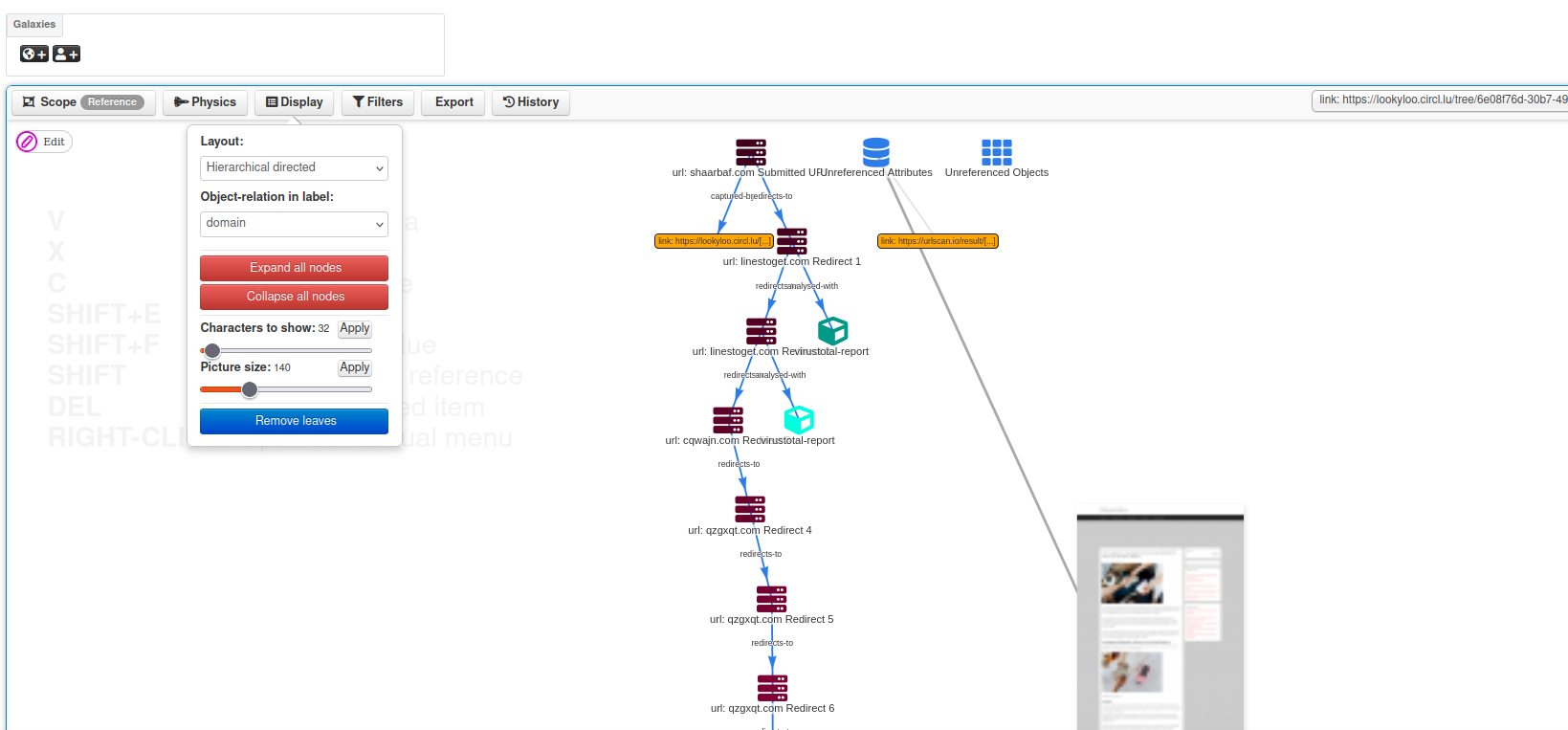
- [event:view] Added option to mass local cluster tag.
Many bugs fixed and minor improvements. Feel free to read the detailed changelog