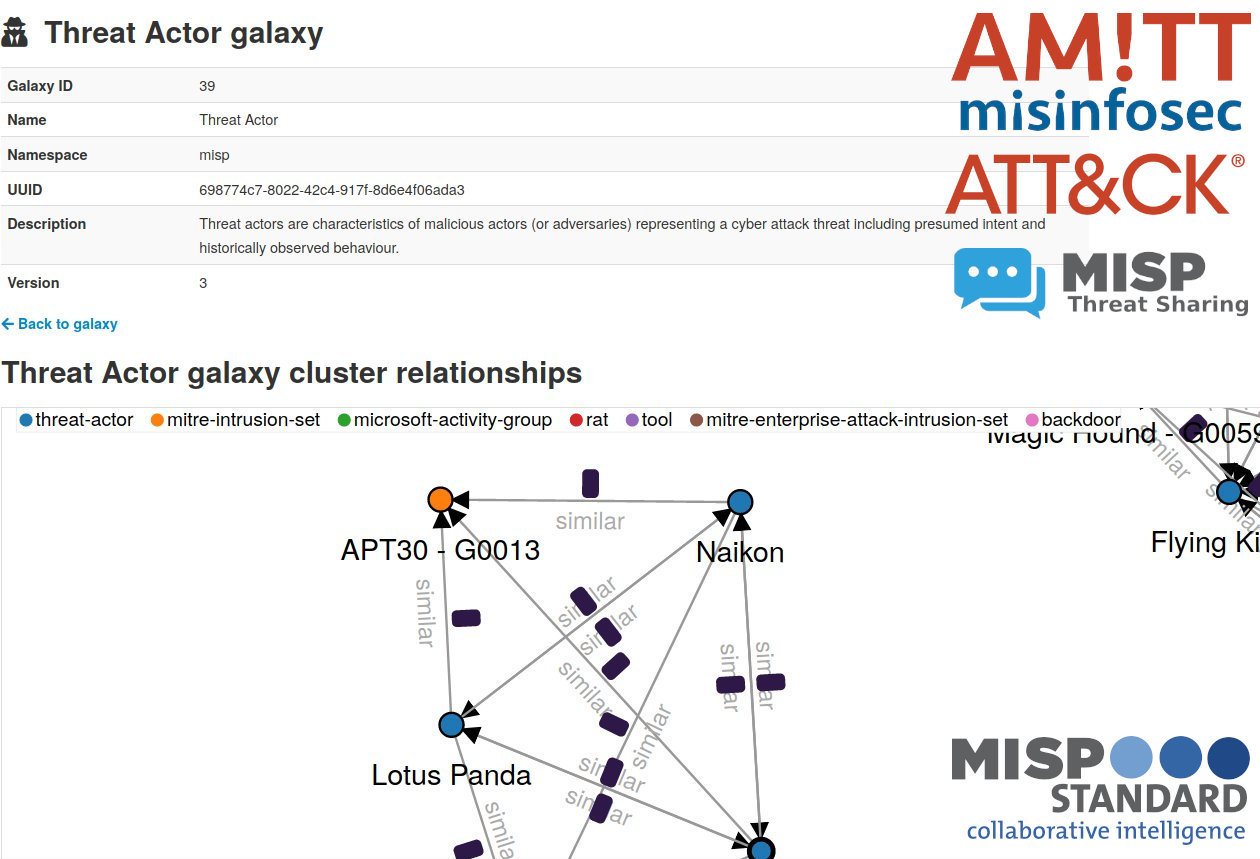
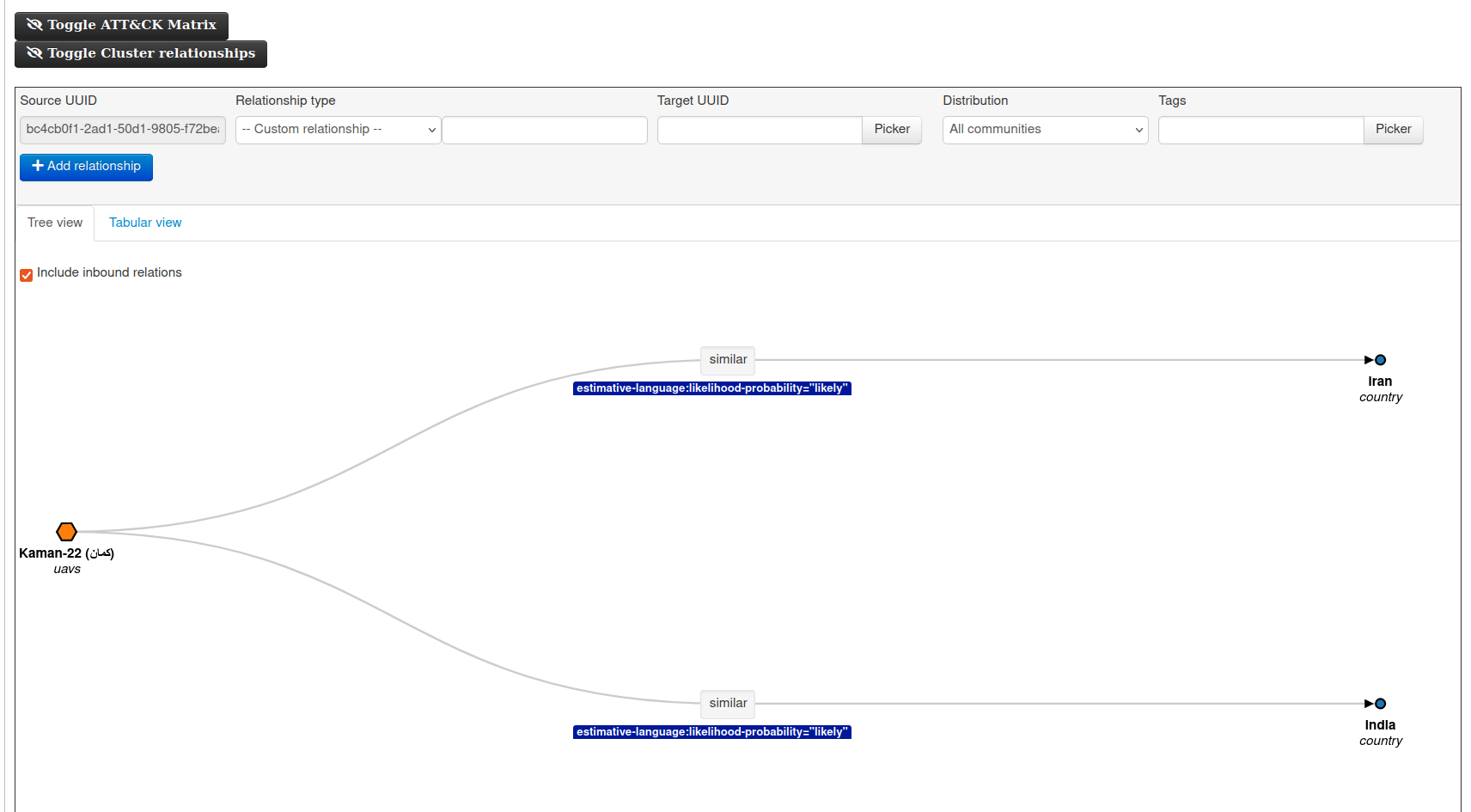
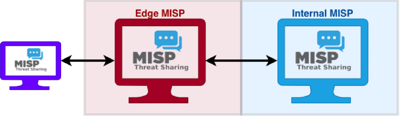
The MISP is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threats about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reversers to support their day-to-day operations to share structured information efficiently.
The Economic Power of Federated Threat Intelligence
The Economic Power of Federated Threat Intelligence
Introduction: Why Policy Matters to Developers
As developers of the MISP project, we spend most of our time thinking about UUIDs, JSON schemas, and API synchronization performance. However, every so often, a piece of academic research comes along that reminds us why this work matters beyond the code.